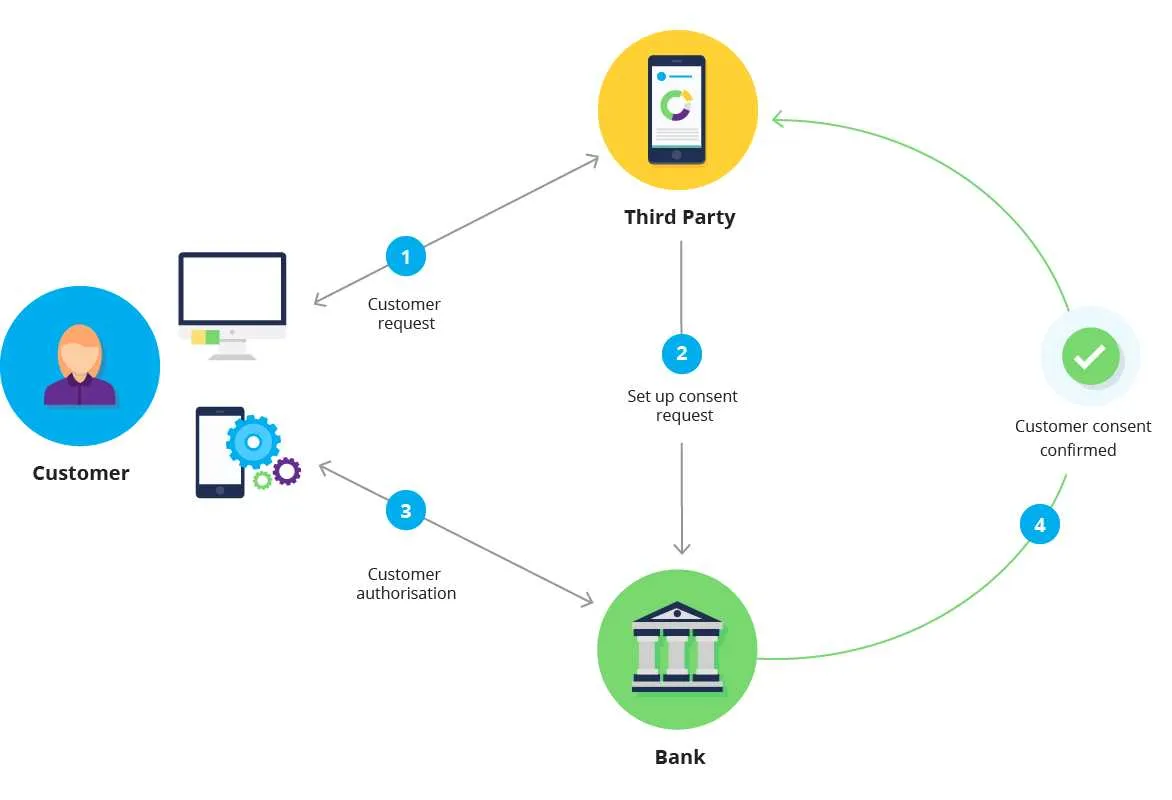
When implementing a reliable method to confirm user identity, focus on ensuring each stage is thoroughly validated. Start by collecting credentials from the user, ensuring they input their information accurately and securely. Always apply encryption during transmission to prevent unauthorized access to sensitive data.
Next, compare the provided information against stored records to verify its accuracy. If there are multiple ways to check identity (such as PINs or biometrics), ensure these checks are performed in sequence, not simultaneously, to reduce vulnerability to attacks.
After the initial check, consider incorporating a second layer of validation, such as a one-time code sent via email or SMS. This additional step drastically reduces the risk of unauthorized access, especially if passwords have been compromised. Ensure the code expires after a short time to prevent reuse.
Finally, once the information has been confirmed, grant access only to authorized areas, keeping sensitive data protected through strict access controls. Reassess and improve each stage periodically to adapt to emerging security threats.
Authentication Workflow Overview

Follow these steps to ensure secure user verification:
- Initiate Request: The user submits login credentials (e.g., username and password).
- Data Transmission: The provided credentials are sent to the server over a secure connection (SSL/TLS).
- Credential Validation: The server checks the user details against the stored records in the database.
- Two-Factor Verification: If enabled, a secondary verification is triggered, such as an OTP sent to the user’s phone or email.
- Session Creation: Upon successful verification, the server generates a session token or cookie, granting access to protected resources.
- Access Confirmation: The system confirms the user’s access, and the session remains active until termination or timeout.
Ensure proper security practices like encrypting sensitive information and using multi-layered protection to strengthen this framework.
Steps Involved in User Authentication Flow
1. User submits credentials: The first step involves entering a username and password, which are sent to the server for verification.
2. Server checks credentials: The server verifies if the provided details match the ones stored in the database. If they match, the user is granted further access.
3. Token generation: Upon successful verification, a unique token is generated. This token will be used for subsequent requests to ensure the user remains authenticated.
4. Session creation: A session is established on the server to track the user’s interaction with the system. The session ID is stored and sent to the client as a cookie.
5. Multi-factor verification (optional): If required, additional verification steps such as SMS codes, email links, or authentication apps are prompted to confirm user identity.
6. Access granted: Once the user’s identity is confirmed and the token is valid, they are allowed access to protected resources.
7. Token expiry and renewal: Tokens have a lifespan and must be refreshed periodically to maintain a secure environment. A renewal request is sent when the token expires.
Visual Representation of Multi-Factor Authentication

Start by displaying each verification step in a clear sequence. Begin with user input for login credentials, followed by a secondary verification, such as a one-time password (OTP) sent via SMS or email. This step should be visually connected to the first, indicating that the second factor relies on the successful entry of the initial credentials.
Primary Input: Show the first step as a simple text box where the user provides their username and password. Use clear labels and minimize distractions around this section.
Secondary Factor: After the primary input, visually link to the second stage, where a verification code is entered. You can illustrate this with a phone or email icon to represent the delivery of the OTP. The design should reflect the dynamic nature of the second factor, perhaps with a timer or countdown to suggest time sensitivity.
Additional Layer: If a biometric factor is involved, use a fingerprint or face recognition icon to indicate this option. Link it visually to the previous steps, showing that it acts as an alternative to the OTP. Each layer should be distinguishable yet interconnected to convey a seamless flow of verification.
Ensure the representation is simple yet informative, with each step easily identifiable. Use arrows or lines to guide the user through each stage. The clarity of these transitions is key to understanding how the different factors work together.
Common Pitfalls in Secure Access Systems

Ensure proper password management. Weak or reused passwords increase vulnerability. Always enforce minimum complexity requirements and regularly prompt for changes.
Failing to implement multi-layer protection, such as two-factor methods, leaves users exposed. Combine knowledge-based verification with an additional factor, like biometrics or one-time codes.
Overlooking session timeouts can lead to unauthorized access. Set appropriate expiration times for inactive sessions and require re-authentication after a certain period.
Relying on outdated hashing techniques, like MD5 or SHA1, is a serious risk. Use more secure algorithms, such as bcrypt, scrypt, or Argon2, to protect stored credentials.
Not properly handling failed attempts can trigger brute-force attacks. Limit retries and implement CAPTCHA or similar mechanisms to block malicious activities.
Ignoring proper logging and monitoring can prevent timely detection of suspicious activities. Log access attempts, especially failed ones, and set up alerts for anomalies.
Neglecting to secure data in transit exposes sensitive information. Always use HTTPS to encrypt communication channels and avoid transmitting credentials in plain text.
Not providing users with clear feedback on their security actions can lead to confusion or poor decisions. Make sure all verification steps are easily understood and provide adequate guidance for each action.