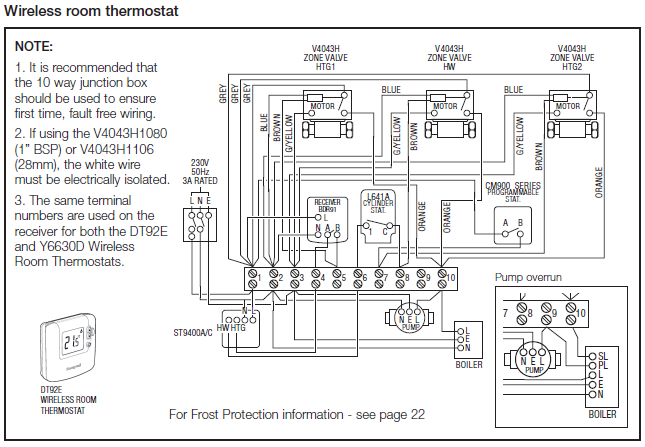
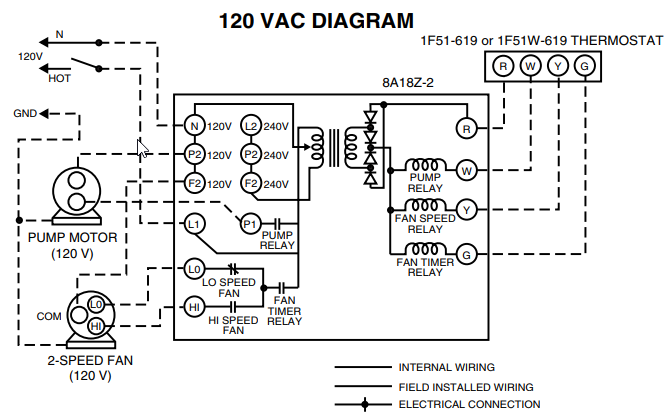
Download scientific diagram | General VDI structure. from publication: Investigation Methodology of a Virtual Desktop Infrastructure for IoT | Cloud computing for.
you’ve been told to roll out VDI – aka that highly riveting technology, virtual desktop infrastructure. VDI Graphics Generation Visio Diagram.
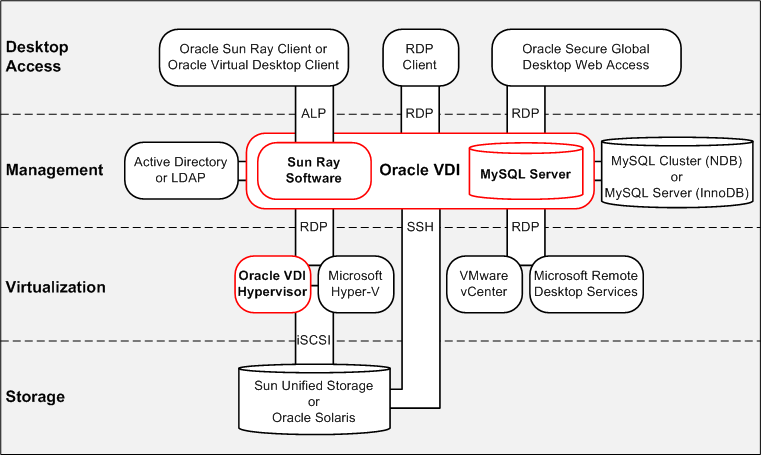
Download scientific diagram | Overall system architecture of virtual desktop infrastructure (VDI). IPS: intrusion prevention system, VPN: virtual private network .
Virtual Desktop Infrastructure, or VDI, refers to the process of running a user desktop inside a virtual machine that lives on a server in the datacenter. It’s a powerful form of desktop virtualization because it enables fully personalized desktops for each user with all the.
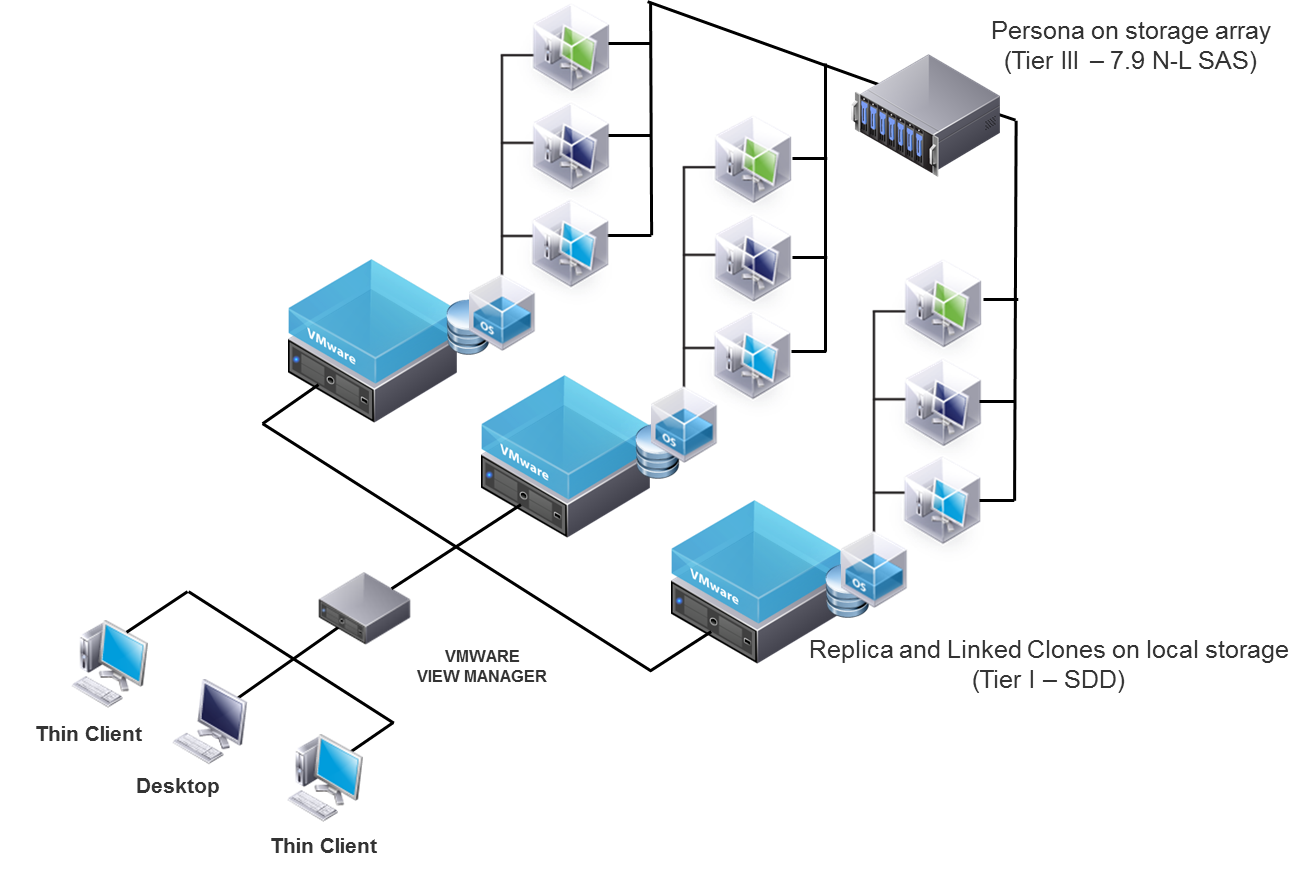
An architectural overview of VDI, what problems it addresses and caveats to look out for.This Cisco Validated Design prescribes a defined set of hardware and software that serves as an integrated foundation for both VMware Horizon Microsoft Windows 7 virtual desktops and VMware Horizon RDSH server desktop sessions based on Microsoft Server R2. Oct 12, · Hi, Ned here. From time to time customers ask us what their options are to document their Active Directory environments – site topologies, domains and trusts, where group policies are linked and what their settings are.
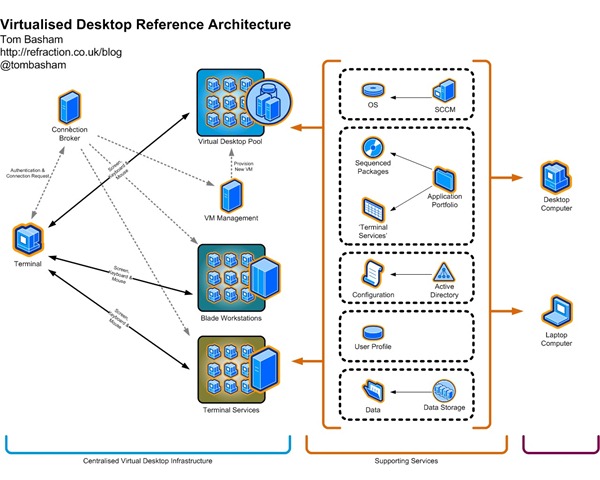
Veeam Veeam Software, a VMware Technology Alliance Premier partner, helps organizations safeguard their investment in virtual infrastructure by providing innovative systems management software. Since at least May , threat actors have targeted government entities and the energy, water, aviation, nuclear, and critical manufacturing sectors, and, in some cases, have leveraged their capabilities to compromise victims’ networks.
By Ray Heffer, VCDX#, VMware EUC Architect.
Back in April , I posted on my blog my original Horizon View network firewall ports diagram. Over the past two years, it’s been used widely both internally at VMware and in the community.Virtual Desktop Infrastructure(VDI) – The Deployment GuysNetwork Protection EOL Policies